Abstract: This article describes how to use secure memory to complete the identification function to protect the FPGA design. While completing the identity recognition feature, it can also implement soft function management and circuit board recognition (IFF) functions. The FPGAs mentioned in this article are all from Xilinx, Inc ..
Motivated to develop electronic products, including embedded FPGA configuration code, the cost is quite high. Therefore, unauthorized institutions should be prevented from copying these designs and configurations to protect the designer ’s intellectual property rights. There are many ways to achieve such a protection function. In high-end FPGAs such as Xilinx Virtex-II® and Virtex-4®, encryption operations for configuration data streams are supported. In this way, these data streams can only work if the FPGA contains the same key. However, this encryption method is not suitable for a wider range of cost-sensitive applications. Therefore, another feasible identification method is used here to prevent accidental copying. This method is applicable to all FPGA families, including the low-end Xilinx Spartan-3® series FPGAs. Prerequisite In the concept of identity recognition, the designer of the FPGA is required to implement the function of communicating with a secure memory for authentication. Figure 1 is a simplified schematic diagram of the design.
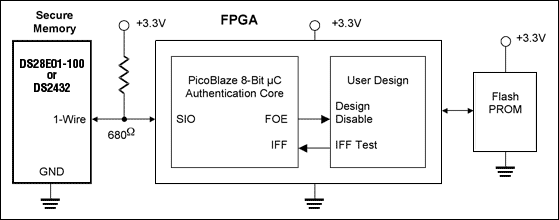
Figure 1. Dallas Semiconductor's 1-Wire memory device provides a simplified block diagram of FPGA security control and protection
The secure storage chip needs to meet the following requirements: Contain the key used for the internal operation of the chip, which is invisible to the outside world. Contains a unique immutable identification number. The identification number can be used to calculate a key that is bound to the device. It can perform HASH operations including keys, random numbers (used as a challenge mechanism), unique identification numbers, and additional data (constants). In order to meet the security required by the application, the HASH algorithm should satisfy: Irreversible—It is computationally infeasible to infer the input data related to it from a HASH result. Anti-collision—It is not feasible to use another set of input data to produce the same HASH result. Has an extremely high avalanche effect—any change in the input data will greatly affect the HASH operation result. SHA-1 algorithm— A comprehensive and widely validated one-way HASH algorithm can meet the above requirements. The algorithm was developed by the US National Bureau of Standards and Technology and adopted by the ISO / IEC 10118-3: 2004 international standard. The public can obtain the algorithm on the NIST website Mathematical principles.
DS28E01-100 and DS2432 are secure memories with built-in SHA-1 algorithm provided by Dallas Semiconductor. The 1-Wire interface of these devices is very suitable for this kind of application, because they only need a pin of FPGA to realize these functions.
FPGAs need to implement the following functions to take advantage of the security features of these devices: Generate random numbers. Know a key used for internal calculation of the chip, and the key is not visible to the outside world. The HASH calculation including the key, random number, additional data, and device identification number is performed like the secure memory. Compare HASH calculation results. The above functional requirements for FPGAs require FPGAs with the performance of microcontrollers, such as PicoBlaze ™, which is Xilinx dedicated to Spartan-3, Virtex-II, Virtex-II Pro®, Virtex-4® FPGA and CoolRunner®-II CPLD Free macro. PicoBlaze uses 192 logic cells, which is only 5% of Spartan-3 XC3S200 devices. Implementation of the technology When the device is powered on, the FPGA reads data from the Flash PROM to configure itself. After the configuration is completed, the microprocessor function of the FPGA is started and performs the authentication work. The authentication work includes the following steps: Generate a set of random numbers and send them to the secure memory as a challenge mechanism (Q). Send instructions to the secure memory, asking it to calculate a HASH result based on the key, challenge mechanism, unique identification number, and fixed additional data. The FPGA itself calculates an expected HASH result (E) based on its own storage key, the same data sent to the secure memory, and fixed additional data. Read the HASH result calculated by the secure storage device as the response (A) and compare it with the expected HASH result (E). If A and E match, the microcontroller considers the circuit to be a "friendly" circuit because it has the correct key. At this time, the FPGA enters a normal working state and turns on / executes all functions in its configuration data. If A and E do not match, the circuit is considered an "enemy" circuit. At this point, the FPGA enters an abnormal operating state and only performs limited functions. What is the safety of this process? For each manufacturing unit, the design owner (OEM) must provide a properly pre-programmed DS28E01-100 or DS2432 for the party (manufacturer or CM) that manufactures products with embedded FPGAs. This one-to-one relationship limits the number of authorized products that CM can manufacture. In order to prevent the CM from tampering with the secure memory (perhaps the CM may apply for more memory on the grounds that the memory is not properly programmed), it is recommended to write protect the key. Even without write protection, there is no need to worry about the security of the data in the 1-Wire EEPROM. It is guaranteed by design that the data in the memory can only be changed if the key is known. This results in a very useful additional function, designers can use this feature to achieve soft feature control: FPGA can turn on / off the corresponding function in FPGA based on the data read from the SHA-1 protected memory.
It is inconvenient or infeasible for the OEM to program such devices before they are distributed to the CM. In order to better solve this problem, Dallas Semiconductor provides OEM customers with SHA-1 key and EEPROM array pre-programming services. Under this service, Dallas Semiconductor's factory registers and configures such devices according to customer requirements, and then Dallas Semiconductor directly ships the device to CM. The advantages of this type of service are as follows: OEMs do not need to disclose the SHA-1 key to the CM. OEM does not need to perform system pre-programming. Only third parties authorized by the OEM can access the registered device. Dallas Semiconductor keeps a record of the number of sending units for the need of OEM auditing. In addition to the security features of SHA-1 itself, the security features of the above-mentioned types of identification and authentication depend on the key, and the key cannot be read from the secure memory or FPGA. Furthermore, the key cannot be discovered by eavesdropping on its configuration data stream when the FPGA is configured. Just like starting from an executable code and trying to crack the C ++ source code of a Windows® application, judging the system design by reverse engineering of the data flow (in this process will try to omit the authentication process) will be a very difficult task task.
Another crucial security factor is the random challenge mechanism Q. A predictable challenge mechanism (such as a constant) will elicit a predictable response result, because the result can be recorded, and then a microcontroller replaces the secure memory. In this predictable situation, the microcontroller can make the FPGA think of it as a "friend" circuit. The random challenge mechanism eliminates this possibility.
If you bind a unique key to each device, you can further increase the security level. The unique key is calculated from the public key (master key), the device's unique identification number, and the constant specified by the application. Under this condition, if one key is cracked, only one device will be affected, so as not to damage the security of the entire system. To achieve this function, the FPGA needs to know the master key and calculate the key used by the memory before calculating the expected response (E). More information The information provided here gives the concept of IFF certification implemented through FPGA and secure memory at a fairly abstract level. For more information, please see the following documents: Application Note 3675, "Protect Your R & D Results-Two-Way Authentication and Software Function Protection" (Security and System Aspects). Application Note 1201, "White Paper 8: 1-Wire SHA-1 Overview" (HASH, SHA-1, trusted token, transaction details, further links to information and product data). XILINX application note XAPP780, "FPGA IFF Copy ProtecTIon Using Dallas Semiconductor / Maxim DS2432 Secure EEPROMs" (successful implementation of the concept, detailed information on how to use FPGA implementation). Secure Hash Standard (English only), Federal Information Processing Standard Publication 180-1. Application Note 178, "Identifying Printed Circuit Boards with 1-Wire Products" (concept, defining data, external measuring points). Application note 3522, "White Paper 9: Is the security of the SHA-1 device still sufficiently secure?" (Preventing "collision", attacks on SHA-1 digests). Conclusion The use of the concept of identity recognition (IFF) can protect intellectual property and prevent it from illegal cloning. This only requires adding a low-cost chip and updating the FPGA configuration code. The secure memory chip and its online programmability allow designers to modify the configuration remotely to achieve software function management without sending technical personnel to the scene. For those secure storage spaces that are not used for software function management, they can be used for circuit board identification.
Motivated to develop electronic products, including embedded FPGA configuration code, the cost is quite high. Therefore, unauthorized institutions should be prevented from copying these designs and configurations to protect the designer ’s intellectual property rights. There are many ways to achieve such a protection function. In high-end FPGAs such as Xilinx Virtex-II® and Virtex-4®, encryption operations for configuration data streams are supported. In this way, these data streams can only work if the FPGA contains the same key. However, this encryption method is not suitable for a wider range of cost-sensitive applications. Therefore, another feasible identification method is used here to prevent accidental copying. This method is applicable to all FPGA families, including the low-end Xilinx Spartan-3® series FPGAs. Prerequisite In the concept of identity recognition, the designer of the FPGA is required to implement the function of communicating with a secure memory for authentication. Figure 1 is a simplified schematic diagram of the design.

Figure 1. Dallas Semiconductor's 1-Wire memory device provides a simplified block diagram of FPGA security control and protection
The secure storage chip needs to meet the following requirements: Contain the key used for the internal operation of the chip, which is invisible to the outside world. Contains a unique immutable identification number. The identification number can be used to calculate a key that is bound to the device. It can perform HASH operations including keys, random numbers (used as a challenge mechanism), unique identification numbers, and additional data (constants). In order to meet the security required by the application, the HASH algorithm should satisfy: Irreversible—It is computationally infeasible to infer the input data related to it from a HASH result. Anti-collision—It is not feasible to use another set of input data to produce the same HASH result. Has an extremely high avalanche effect—any change in the input data will greatly affect the HASH operation result. SHA-1 algorithm— A comprehensive and widely validated one-way HASH algorithm can meet the above requirements. The algorithm was developed by the US National Bureau of Standards and Technology and adopted by the ISO / IEC 10118-3: 2004 international standard. The public can obtain the algorithm on the NIST website Mathematical principles.
DS28E01-100 and DS2432 are secure memories with built-in SHA-1 algorithm provided by Dallas Semiconductor. The 1-Wire interface of these devices is very suitable for this kind of application, because they only need a pin of FPGA to realize these functions.
FPGAs need to implement the following functions to take advantage of the security features of these devices: Generate random numbers. Know a key used for internal calculation of the chip, and the key is not visible to the outside world. The HASH calculation including the key, random number, additional data, and device identification number is performed like the secure memory. Compare HASH calculation results. The above functional requirements for FPGAs require FPGAs with the performance of microcontrollers, such as PicoBlaze ™, which is Xilinx dedicated to Spartan-3, Virtex-II, Virtex-II Pro®, Virtex-4® FPGA and CoolRunner®-II CPLD Free macro. PicoBlaze uses 192 logic cells, which is only 5% of Spartan-3 XC3S200 devices. Implementation of the technology When the device is powered on, the FPGA reads data from the Flash PROM to configure itself. After the configuration is completed, the microprocessor function of the FPGA is started and performs the authentication work. The authentication work includes the following steps: Generate a set of random numbers and send them to the secure memory as a challenge mechanism (Q). Send instructions to the secure memory, asking it to calculate a HASH result based on the key, challenge mechanism, unique identification number, and fixed additional data. The FPGA itself calculates an expected HASH result (E) based on its own storage key, the same data sent to the secure memory, and fixed additional data. Read the HASH result calculated by the secure storage device as the response (A) and compare it with the expected HASH result (E). If A and E match, the microcontroller considers the circuit to be a "friendly" circuit because it has the correct key. At this time, the FPGA enters a normal working state and turns on / executes all functions in its configuration data. If A and E do not match, the circuit is considered an "enemy" circuit. At this point, the FPGA enters an abnormal operating state and only performs limited functions. What is the safety of this process? For each manufacturing unit, the design owner (OEM) must provide a properly pre-programmed DS28E01-100 or DS2432 for the party (manufacturer or CM) that manufactures products with embedded FPGAs. This one-to-one relationship limits the number of authorized products that CM can manufacture. In order to prevent the CM from tampering with the secure memory (perhaps the CM may apply for more memory on the grounds that the memory is not properly programmed), it is recommended to write protect the key. Even without write protection, there is no need to worry about the security of the data in the 1-Wire EEPROM. It is guaranteed by design that the data in the memory can only be changed if the key is known. This results in a very useful additional function, designers can use this feature to achieve soft feature control: FPGA can turn on / off the corresponding function in FPGA based on the data read from the SHA-1 protected memory.
It is inconvenient or infeasible for the OEM to program such devices before they are distributed to the CM. In order to better solve this problem, Dallas Semiconductor provides OEM customers with SHA-1 key and EEPROM array pre-programming services. Under this service, Dallas Semiconductor's factory registers and configures such devices according to customer requirements, and then Dallas Semiconductor directly ships the device to CM. The advantages of this type of service are as follows: OEMs do not need to disclose the SHA-1 key to the CM. OEM does not need to perform system pre-programming. Only third parties authorized by the OEM can access the registered device. Dallas Semiconductor keeps a record of the number of sending units for the need of OEM auditing. In addition to the security features of SHA-1 itself, the security features of the above-mentioned types of identification and authentication depend on the key, and the key cannot be read from the secure memory or FPGA. Furthermore, the key cannot be discovered by eavesdropping on its configuration data stream when the FPGA is configured. Just like starting from an executable code and trying to crack the C ++ source code of a Windows® application, judging the system design by reverse engineering of the data flow (in this process will try to omit the authentication process) will be a very difficult task task.
Another crucial security factor is the random challenge mechanism Q. A predictable challenge mechanism (such as a constant) will elicit a predictable response result, because the result can be recorded, and then a microcontroller replaces the secure memory. In this predictable situation, the microcontroller can make the FPGA think of it as a "friend" circuit. The random challenge mechanism eliminates this possibility.
If you bind a unique key to each device, you can further increase the security level. The unique key is calculated from the public key (master key), the device's unique identification number, and the constant specified by the application. Under this condition, if one key is cracked, only one device will be affected, so as not to damage the security of the entire system. To achieve this function, the FPGA needs to know the master key and calculate the key used by the memory before calculating the expected response (E). More information The information provided here gives the concept of IFF certification implemented through FPGA and secure memory at a fairly abstract level. For more information, please see the following documents: Application Note 3675, "Protect Your R & D Results-Two-Way Authentication and Software Function Protection" (Security and System Aspects). Application Note 1201, "White Paper 8: 1-Wire SHA-1 Overview" (HASH, SHA-1, trusted token, transaction details, further links to information and product data). XILINX application note XAPP780, "FPGA IFF Copy ProtecTIon Using Dallas Semiconductor / Maxim DS2432 Secure EEPROMs" (successful implementation of the concept, detailed information on how to use FPGA implementation). Secure Hash Standard (English only), Federal Information Processing Standard Publication 180-1. Application Note 178, "Identifying Printed Circuit Boards with 1-Wire Products" (concept, defining data, external measuring points). Application note 3522, "White Paper 9: Is the security of the SHA-1 device still sufficiently secure?" (Preventing "collision", attacks on SHA-1 digests). Conclusion The use of the concept of identity recognition (IFF) can protect intellectual property and prevent it from illegal cloning. This only requires adding a low-cost chip and updating the FPGA configuration code. The secure memory chip and its online programmability allow designers to modify the configuration remotely to achieve software function management without sending technical personnel to the scene. For those secure storage spaces that are not used for software function management, they can be used for circuit board identification.
1-3HP Compressor Series Sealed Terminal Blocks
1-3Hp Compressor Series Sealed Terminal Blocks,Refrigerator Compressor Sealing Terminal,Ice Machine Compressor Sealing Terminal,Mini Compressor Feedthroughs For Wine Cabinet
Shenzhen Capitol Micro-Electronics Co.,LTD , https://www.capitolgtms.com