On the morning of May 14, 360 threat intelligence center released the WannaCrypt (Eternal Blue) extortion worm latest situation, as of May 13 at 20:00, there are also 29,372 organizations in the country organized hundreds of thousands of machine infections, including education research The recruitment of the agency 4341 was the hardest hit of the incident.
According to the 360 ​​threat intelligence center statistics, in just over a day, WannaCrypt (Eternal Blue) extortion worm has attacked more than 100,000 companies and public organizations in nearly 100 countries, including 1,600 U.S. organizations and 11,200 Russian organization.
Infected organizations and institutions in China have covered almost all areas. The scope of influence has spread across universities, railway stations, self-service terminals, postal services, gas stations, hospitals, and government service terminals. The number of infected computers is still growing. .
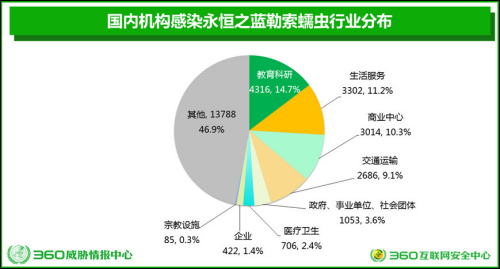
From the perspective of industry distribution, education and scientific research institutions have become the biggest disaster areas. A total of 4,316 IPs of educational institutions were found to be infected with the Eternal Blue ransomware worm, accounting for 14.7%; followed by life service organizations, 3302, accounting for 11.2%; and commercial centers (office buildings, office buildings, shopping centers, etc.) 3014 , accounting for 10.3%, transportation 2686, accounting for 9.1%. Another 1053 government, public institutions and social organizations, 706 medical and health institutions, 422 companies, and 85 religious facilities IP have been found infected with the eternal blue ransom worm.
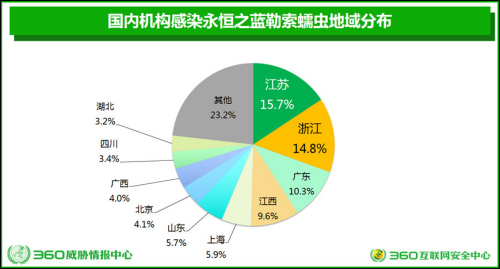
Among the affected regions, Jiangsu, Zhejiang, Guangdong, Jiangxi, Shanghai, Shandong, Beijing, and Guangxi rank the top eight.
WannaCrypt (Eternal Blue) Extortion Worm is a ransom worm attack that began suddenly on May 12th in the world, including the British medical system, the express company FedEx, the Russian Ministry of the Interior, the Russian telecommunications company Megafon, and Telefonica. WannaCrypt (Eternal Blue) extortion worm uses the eternal blue attack program in the leaked NSA cyber arsenal. This is the world's first civilian use of NSA cybermunitions. A month ago, the fourth batch of NSA-related cyber attack tools and documents were published by the Shadow Brokers organization and included remote command execution tools involving multiple Windows system services (SMB, RDP, IIS), including the “Eternal Blue†attack. program.
In view of WannaCrypt's (Eternal Blue) extortion worm impact has shown a serious situation, 360 corporate security specifically for the domestic large-scale institutions released the Eternal Blue ransom worm emergency handling manual, to help large-scale domestic institutions to prevent the eternal blue ransom worm.
It is recommended that all major domestic institutions adopt the following emergency measures.
1, confirm the scope of influence
Potentially affected system validation
Scan the intranet, and discover all terminals and servers that open the 445 SMB service port. Check whether the MS17-010 patch is installed for Win7 and later systems. If it is not installed, it is affected by threats. Windows XP/2003 under Win7 is currently not patched, as long as the SMB service is enabled.
Infected worm system discovery
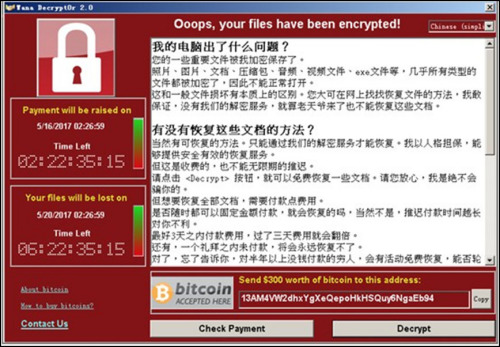
The infected machine screen will display the following ransom payment interface:
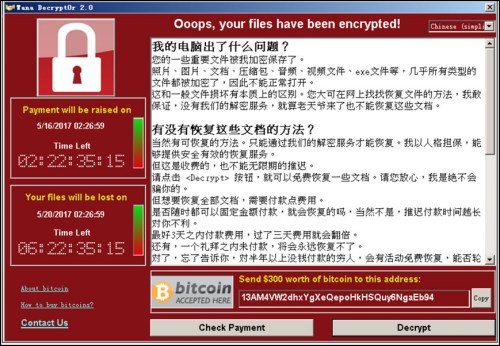
360 Enterprise Security The Sky Eye System has updated the detection rules and automatically updates the rules to generate an alert for the infected system.
2. Emergency disposal methods
At the network level, worms that use vulnerabilities to spread attacks begin to flood. 360 Enterprise Security It is strongly recommended that network administrators block access to port 445 on firewalls at network boundaries. If there are IPS and 360-day embankment intelligence firewalls on the boundary, For devices, upgrade the detection rules of the device to the latest version and set the blocking of corresponding vulnerability attacks until you confirm that the computers on the network have installed the MS17-010 patch or have closed the server service.
At the terminal level, if you find that port 445 is open, you need to shut down the Server service.
360 Corporate Security The Tianqing team has developed an immunization tool for WannaCry's ransomware worm. After the program is run on a computer, existing worms will not infect the system.
360 Enterprise Security Next Generation Wisdom Firewall (NSG3000/5000/7000/9000 Series) and Next-Generation Extreme Firewall (NSG3500/5500/7500/9500 Series) Product Family, worm variants have been completed by updating IPS signature database and application signature database For protection and identification, users are strongly encouraged to upgrade the IPS signature database and application signature database to the version as soon as possible.
Isolation is recommended for machines that have been infected with ransom worms.
3, the cure method
For Win7 and above operating systems, Microsoft has released patch MS17-010 to fix the system flaw of the "Everlasting Blue" attack. Please install this patch on your computer immediately.
For Windows XP, 2003, and other Microsoft machines that no longer provide security updates as planned, Microsoft has provided special patches for this time-influenced network attack. Please go to download and install.
For security practices based on privilege mitigation, it is recommended that users shut down Server services that are not required to be used. For the operation method, see the section on emergency measures.
4, recovery stage
It is recommended to back up data immediately for important business systems, perform system image mirroring for important business terminals, and make enough system recovery disks or devices to replace them.
Charging Cable,Car Charging Cable,Car Battery Cable,Car Charging Wire
Dong guan Sum Wai Electronic Co,. Ltd. , https://www.sw-cables.com